ICMP redirect messages are used by routers to inform hosts that there is a better next hop to reach a certain destination. Take a look at the following topology for an example:

Let me explain the topology above:
- R1, R2 and the host are connected to the 192.168.12.0 /24 network.
- R1 is connected to an ISP to reach the Internet, it will use a default route to get there.
- R2 is connected to R3, there’s a server behind R3 that is reachable at IP address 3.3.3.3.
- R1 uses a static route to reach 3.3.3.3.
- Hosts on the 192.168.12.0 /24 network will use R1 as their default gateway.
Whenever our host tries to reach 3.3.3.3 then it will send its packets to its default gateway. R1 however has a static route for this destination that points to R2.
This is a bit pointless since packets from the host will enter and exit the same interface on R1. To prevent this from happening, our routers can use ICMP redirect.
When R1 receives IP packets from the host with 3.3.3.3 as its destination then it will send an ICMP redirect message telling the host to use R2 as their gateway for this destination. Most hosts will respect these ICMP messages and will use R2 to reach 3.3.3.3 from now on.
Cisco IOS routers will send ICMP redirects when the following conditions are met:
- The IP packet should be received and transmitted on the same interface.
- The source IP address of the incoming packet should be on the same subnet as the new next hop IP address.
- The IP packet doesn’t use source routing.
- ICMP redirect has to be enabled, on Cisco IOS routers this is enabled by default.
Let’s take a look at some configuration examples so you can see how this works. I’ll use the following topology for this:

I will use the same topology but I’ve added a couple of hosts:
- Windows 8 host
- Linux host
- Cisco router as host (IP routing disabled)
Let’s see how these hosts act when they receive an ICMP redirect.
Configuration
First let me show you the routing tables of R1 and R2:
R1#show ip route static | begin via
S* 0.0.0.0/0 [1/0] via 192.168.14.4
3.0.0.0/32 is subnetted, 1 subnets
S 3.3.3.3 [1/0] via 192.168.12.2
R1 has two static routes, a default route and an entry for 3.3.3.3. Here’s R2:
R2#show ip route static | begin via
S 3.3.3.3 [1/0] via 192.168.23.3
R2 only has a static route for 3.3.3.3 with R3 as its next hop.
Let’s enable ICMP debugging on R1, this will show us when R1 is sending ICMP redirects:
R1#debug ip icmp
ICMP packet debugging is on
Now let’s generate some traffic from our hosts.
Windows Host
We will start with the Windows host. Let’s send a ping to 3.3.3.3:
C:Usersvmware>ping 3.3.3.3
Pinging 3.3.3.3 with 32 bytes of data:
Reply from 3.3.3.3: bytes=32 time=4ms TTL=254
Reply from 3.3.3.3: bytes=32 time=1ms TTL=254
Reply from 3.3.3.3: bytes=32 time=2ms TTL=254
Reply from 3.3.3.3: bytes=32 time=2ms TTL=254
Ping statistics for 3.3.3.3:
Packets: Sent = 4, Received = 4, Lost = 0 (0% loss),
Approximate round trip times in milli-seconds:
Minimum = 1ms, Maximum = 4ms, Average = 2ms
We don’t see anything spectacular on the host but R1 generates the following message:
R1#
ICMP: redirect sent to 192.168.12.100 for dest 3.3.3.3, use gw 192.168.12.2
It’s telling our Windows host to use R2 as the gateway to reach 3.3.3.3. Here’s what it looks like in wireshark:
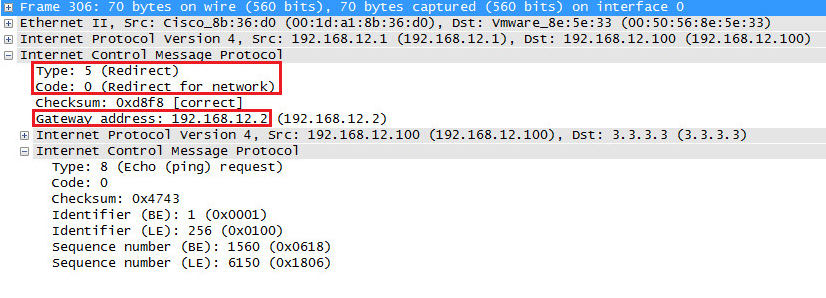
Above you can see that the ICMP type 5 message is an ICMP redirect. Now take a look at the next packet that the host will send:
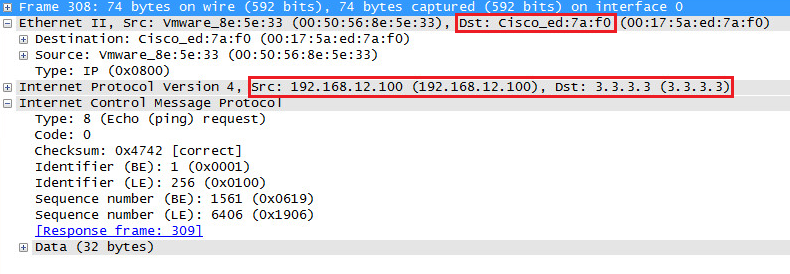
This IP packet that is destined for 3.3.3.3 now uses the MAC address of R2 as the destination. We can confirm this by checking the MAC address on R2:
R2#show interfaces FastEthernet 0/0 | include address
Hardware is MV96340 Ethernet, address is 0017.5aed.7af0 (bia 0017.5aed.7af0)
The windows host doesn’t really notify us that its traffic has been redirected but you can see that something happened behind the scenes.
Supposedly you should be able to see an entry in the windows routing table that you can see with the route print command. I tried this on a windows 7 and 8 host but couldn’t find anything…
Let’s try another host!
Linux Host
This time we’ll try a Linux host, I used the desktop version of Ubuntu. When we send a ping we see this:
$ ping 3.3.3.3
PING 3.3.3.3 (3.3.3.3) 56(84) bytes of data.
From 192.168.12.1: icmp_seq=1 Redirect Network(New nexthop: 192.168.12.1)
64 bytes from 192.168.12.1: icmp_seq=1 ttl=254 time=4.56 ms
64 bytes from 192.168.12.1: icmp_seq=2 ttl=254 time=1.25 ms
This is great, our linux host tells us that it received the ICMP redirect. You can also verify this with the following command:
$ ip route get 3.3.3.3
3.3.3.3 via 192.168.12.2 dev eth0 src 192.168.12.101
cache <redirected>
Above you see a cached entry for 3.3.3.3. Whenever we try to reach this IP address, we’ll use R2 as the default gateway.
Cisco Device
Last but not least, let’s see what a Cisco device does with the ICMP redirect. I will use a router that has IP routing disable:
Host(config)#ip default-gateway 192.168.12.1
Host(config)#no ip routing
Here’s how you can verify that this router doesn’t have a routing table anymore:
Host#show ip route
Default gateway is 192.168.12.1
Host Gateway Last Use Total Uses Interface
ICMP redirect cache is empty
There’s no routing table and this device will use 192.168.12.1 as its default gateway. It also shows us the ICMP redirect cache which is empty at the moment. Let’s send a ping to 3.3.3.3:
Host#ping 3.3.3.3
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 3.3.3.3, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/202/1000 ms
Now take a look at the routing table:
Host#show ip route
Default gateway is 192.168.12.1
Host Gateway Last Use Total Uses Interface
3.3.3.3 192.168.12.2 0:00 12 FastEthernet0/0
The router stored an entry for 3.3.3.3 in its ICMP redirect cache. You can verify this with another command:
Host#show ip redirects
Default gateway is 192.168.12.1
Host Gateway Last Use Total Uses Interface
3.3.3.3 192.168.12.2 0:07 12 FastEthernet0/0
The show ip redirects command will tell us the same thing.
Conclusion
You have now seen how ICMP redirects help to redirect traffic to another gateway. Although this might sound useful, it’s also a security risk. These messages are very simple to spoof and all our hosts accepted the redirect packet without any issues. For this reason it’s probably a good idea to disable this on your hosts.
You can also disable it on your Cisco IOS routers:
R1(config)#interface FastEthernet 0/0
R1(config-if)#no ip redirects
If you use the no ip redirects command then it will no longer send ICMP redirect messages to hosts.
That’s all we have for now, I hope this has been useful! If you have any questions, feel free to leave a comment!
No comments:
Post a Comment